IT Department Role Optimization
In an SMB, roles may be filled by 1 or more people – but there more like hats – and a single person may be wearing many, many hats. One-man IT shop? You’re a hat shop. Dynamic duo of IT crime fighting? Hopefully you have a Batcave for your hats.
In large corporations you have a complex organizational structure within the IT department, it might be a hierarchical tree or a wheel of distributed teams serving different operational needs. Within those large structures, roles can be generally defined by a person or group of people and what they are responsible for.
In a medium-sized team, the hats will shift around more often as there are more people to wear them but the organization is not so large that it is unable to adapt to change. Role optimization in a team of 3-10 individuals is a process where the roles are all independently examined, along with the strengths and interests of the team members and the potential future needs of the organization as a whole.
It’s the time of year where I’m finishing up the post-mortem on the previous year and setting out plans to make the changes for the current year to improve the future 2-3 years. This means I’m working through our role optimization. These roles involve technology, but that does not mean the roles are necessarily held within the IT department. The roles could be managed my another department or outsourced to a managed services company.
The following roles are being examined:
From this list of roles, you create a table with a column for each IT contributor/person and mark each for the hats (roles) they are c_urrently formally wearing_. Might look something like this:
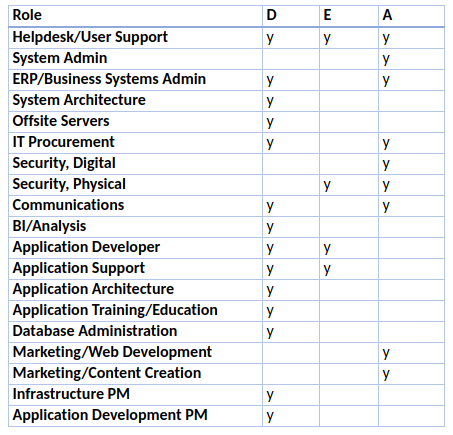 ][1]
][1]
Using a grade system of A-C or 1-3, consider how the roles would or do fit the individual at this time. Give scores for every role that the individual formally holds, has a relative skillset, did handle, or does handle from time to time. Look at the chart a few times to make sure singular incidents aren’t pushing the scale one way or another. Highlight the low scores in red and the high scores in green.
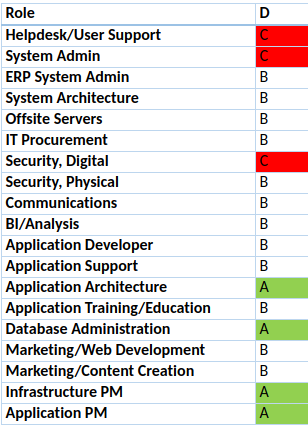 ][2]
][2]
If someone is in the red – they need to improve or not be involved in that role. The other people that share that hat with them will be grateful to not get it back all dirtied and soiled. However, this might mean that other roles need to shift around.
Depending on the organization, some roles may be bigger than others. For example, _Application Developer _is pretty much a 10-gallon hat on the IT team I am evaluating here. Individual E could focus most of his time here and still be a valued and contributing member of the group. Individual _A _is a younger member of the group and is looking for direction on his growth and development. I see a clear need for our team to have someone who excels in system architecture and offsite servers.
The weakness that is exposing us at this time is in Application Support and Application Training/Education. For individual D, it becomes a capacity issue. Individuals _E _and _A _are not quite up to speed on the skillset needed.
Fortunately, all marketing roles are not within the IT team at this time. However, it is good to be aware of them because as our organization evolves, it might be needed.
Where do we go from here?
Reorient the team and set deadlines for improvements where needed. With quarterly formal check-ins, you can reflect on the roles that the individual is responsible for.
Long-range planning involves making educated guesses about the organization’s needs and the capabilities of the individuals. You can and should ask an individual which hats they would like to be wearing down the road, but you also need to be prepared to share guidance and feedback on their journey. You should also be aware of what it would take to replace someone should they leave the team or if they are no longer a good fit.
There is also an element of succession planning to this exercise. As roles expand and contract, the team will have to build along with it. If you need to add a new individual and increase the team size, where does that building block best fit?
 ][3]
][3]
Remember how I mentioned that large organizations may have complex IT department structures? Medium-sized IT team structures aren’t any less complicated, there are just fewer people to comprise the team. The best fits for these teams will be individuals who enjoy keeping a hat rack at their desk.